Understanding AMSI: The Antimalware Scan Interface in Windows Systems
The Antimalware Scan Interface (AMSI) is a key element in Windows’ cybersecurity framework, often working behind the scenes to protect your system from malicious software. It serves as an intermediary between software and installed antivirus solutions, providing an extra layer of security for the system. Introduced in 2015 with Windows 10, AMSI has been an integral part of subsequent Windows versions.
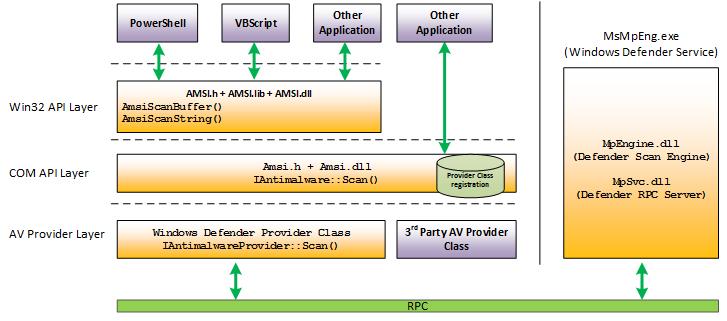
Structurally, AMSI functions as an integrated application equipped with an open system API. This allows other software to send samples of code to an installed antivirus solution for analysis, essentially making AMSI a watchdog that monitors incoming data for any malware-like activities.
The types of software that can interact with AMSI are broadly divided into two categories:
- Third-party or Microsoft software that scans incoming data.
- Antivirus software, other than Windows Defender, that leverages AMSI solely for analysis.
This open interaction model means that organizations are not restricted to a particular antivirus vendor.
AMSI supports a call structure using both WIN32 AMSI API interfaces and AMSI COM interfaces. It allows not only file and memory scans but also the ability to check source URLs and IP addresses for potential risks.
One of the specific targets for AMSI is the prevention of fileless attacks. A files malware attack, is a type of cyberattack that doesn’t rely on traditional executable files to infect a system. Instead, it utilizes tools and processes that are already part of the operating system or executes code directly in memory. Because it doesn’t download or store files on the disk, this type of threat can be more challenging to detect and mitigate using conventional antivirus and anti-malware software, which often focuses on scanning and analyzing files. Additionally, it employs four mechanisms for in-depth analysis of files:
- Static (Signature-based) Analysis
- Dynamic Analysis
- Unpacking Mechanism
- Behavioral (Heuristic) Analysis
For scripting languages that don’t require files to be saved on disk, amsi.dll was developed to enable signature analysis both before and after code execution, and also during the .NET process execution.
Here’s an illustration of the AMSI architecture, as shown on official Microsoft public documentation.
Components Scanned by AMSI
By default, Windows Defender uses AMSI’s API to scan a variety of components, including but not limited to:
- PowerShell (Version 2.0 and above)
- User Account Control (UAC) actions
- Windows Script Host
- JavaScript
- Visual Basic Script
- Office Program Macro Scripts
- .NET Framework
- Windows Management Instrumentation (WMI)
Bypassing AMSI
While AMSI offers a robust layer of security, it’s worth noting that no system is impregnable. Security researchers and hackers often find methods to bypass AMSI. Few examples, on how this can be achieved:
DebugAmsi
Amsi-Killer
Amsi Bypass In 2023
Amsi-Bypass-Powershell